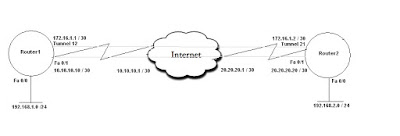
DMVPN between Router 1 with public static ip and Router 2 with DSL line with dynamic ip
Router 1 - fa0 - Public internet connection ( 20.20.20.2/30) - { internet cloud} - ADSL -(192.168.1.2/24) fa1 - Router 2
Router 1
conf t
crypto isakmp policy 25
encr 3des
hash md5
authentication pre-share
crypto isakmp key r1-r2dmvpn address 0.0.0.0 0.0.0.0
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac
mode transport
mode transport
crypto ipsec profile DMVPN
set security-association lifetime seconds 28800
set transform-set ESP-AES-SHA
interface Tunnel0set security-association lifetime seconds 28800
set transform-set ESP-AES-SHA
ip address 10.10.10.1 255.255.255.0
ip mtu 1400
ip nhrp authentication VPNkey
ip nhrp map multicast dynamic
ip nhrp network-id 123456
ip nhrp holdtime 360
ip virtual-reassembly
ip tcp adjust-mss 1360
load-interval 60
delay 1000
qos pre-classify
tunnel source FastEthernet0
tunnel mode gre multipoint
tunnel key 100001
tunnel protection ipsec profile DMVPN shared
end
ip mtu 1400
ip nhrp authentication VPNkey
ip nhrp map multicast dynamic
ip nhrp network-id 123456
ip nhrp holdtime 360
ip virtual-reassembly
ip tcp adjust-mss 1360
load-interval 60
delay 1000
qos pre-classify
tunnel source FastEthernet0
tunnel mode gre multipoint
tunnel key 100001
tunnel protection ipsec profile DMVPN shared
end
Configuration on Router 2
conf t
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 5
encr aes 256
authentication pre-share
group 5
crypto isakmp key r1-r2dmvpn address 20.20.20.2
crypto ipsec security-association replay window-size 1024
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac
mode transport
mode transport
crypto ipsec profile DMVP
set security-association lifetime seconds 28800
set transform-set ESP-AES-SHA
set security-association lifetime seconds 28800
set transform-set ESP-AES-SHA
interface Tunnel1
ip address 10.10.10.2 255.255.255.0
ip mtu 1400
ip nhrp authentication VPNkey
ip nhrp map 10.10.10.1 20.20.20.2
ip nhrp network-id 123456
ip nhrp holdtime 360
ip nhrp nhs 10.10.10.1
ip nhrp registration no-unique
ip tcp adjust-mss 1360
delay 1000
qos pre-classify
tunnel source FasteEthernet 1
tunnel mode gre multipoint
tunnel key 100001
tunnel protection ipsec profile DMVPN shared
ip address 10.10.10.2 255.255.255.0
ip mtu 1400
ip nhrp authentication VPNkey
ip nhrp map 10.10.10.1 20.20.20.2
ip nhrp network-id 123456
ip nhrp holdtime 360
ip nhrp nhs 10.10.10.1
ip nhrp registration no-unique
ip tcp adjust-mss 1360
delay 1000
qos pre-classify
tunnel source FasteEthernet 1
tunnel mode gre multipoint
tunnel key 100001
tunnel protection ipsec profile DMVPN shared
end